Table of Contents
Authlete is a managed-cloud/on-prem solution that provides Web APIs to implement OAuth 2.0 and OpenID Connect. Using our Web APIs, you can easily get the functionality of OAuth 2.0 and OpenID Connect.
A company has to implement OAuth 2.0 (and OpenID Connect) as prerequisites to provide Web APIs of its service. However, it requires enormous time and effort to implement the specifications. Also, managing data related to the specifications is an annoyance. This hurdle could prove fatal to service providers who compete on time to market and/or cannot afford to implement the prerequisites only with their developer resources.
It is Authlete that solves the problem. Authlete does support an overwhelming number of related specifications and host related data. Authlete users can start to implement Web APIs of their services without being bothered with the prerequisites.
Authlete is a backend as a service and provides APIs that help you to implement OAuth and OpenID Connect. Authlete works behind your web service and does not interact directly with your end-users, OAuth clients, or relying parties.
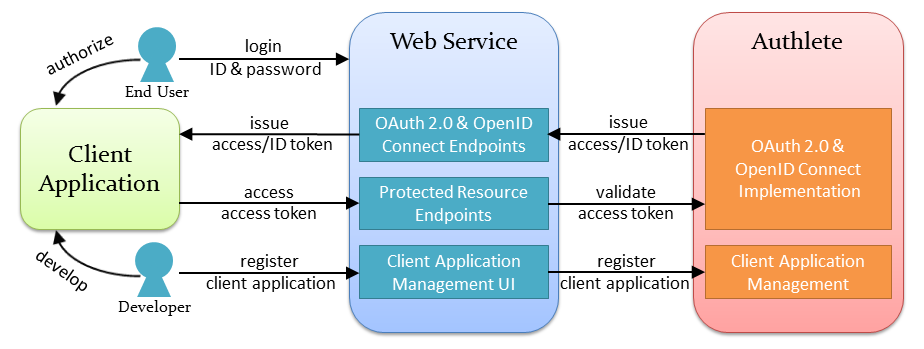
The Authlete “semi-hosted” architecture enables you to:
Open all tabs | Close all tabs
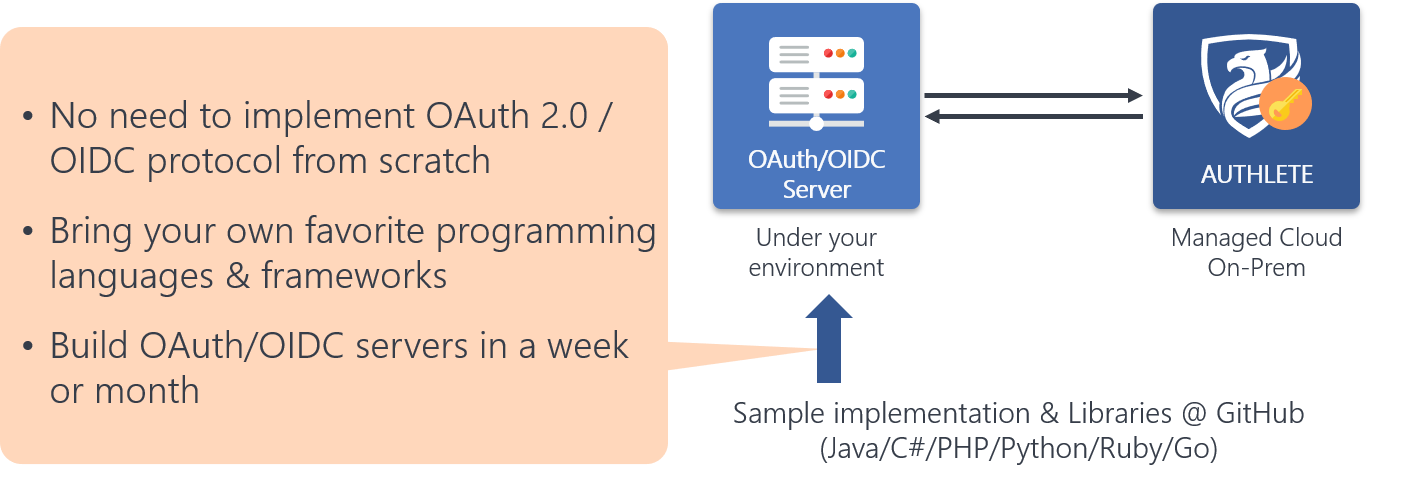
Authlete has designed and implemented all functions necessary to implement an OAuth 2.0 & OpenID Connect server as Web APIs. On top of the functions to manage metadata of client applications and authorization servers, Authlete also provides functions to implement endpoints such as an authorization endpoint and a token endpoint.
This unique architecture enables developers to use any programming language, including Java, Ruby, PHP and C#. Our OSS libraries and sample implementations will help you build OAuth/OIDC servers within a few days or weeks.
OAuth endpoints, such as authorization endpoint, will be placed in your environment, not ours. Therefore, you can customize UI and UX with no limit. For example, you can separate the authentiation page from authorization page, or you can allow your end-users to choose scopes to be granted.

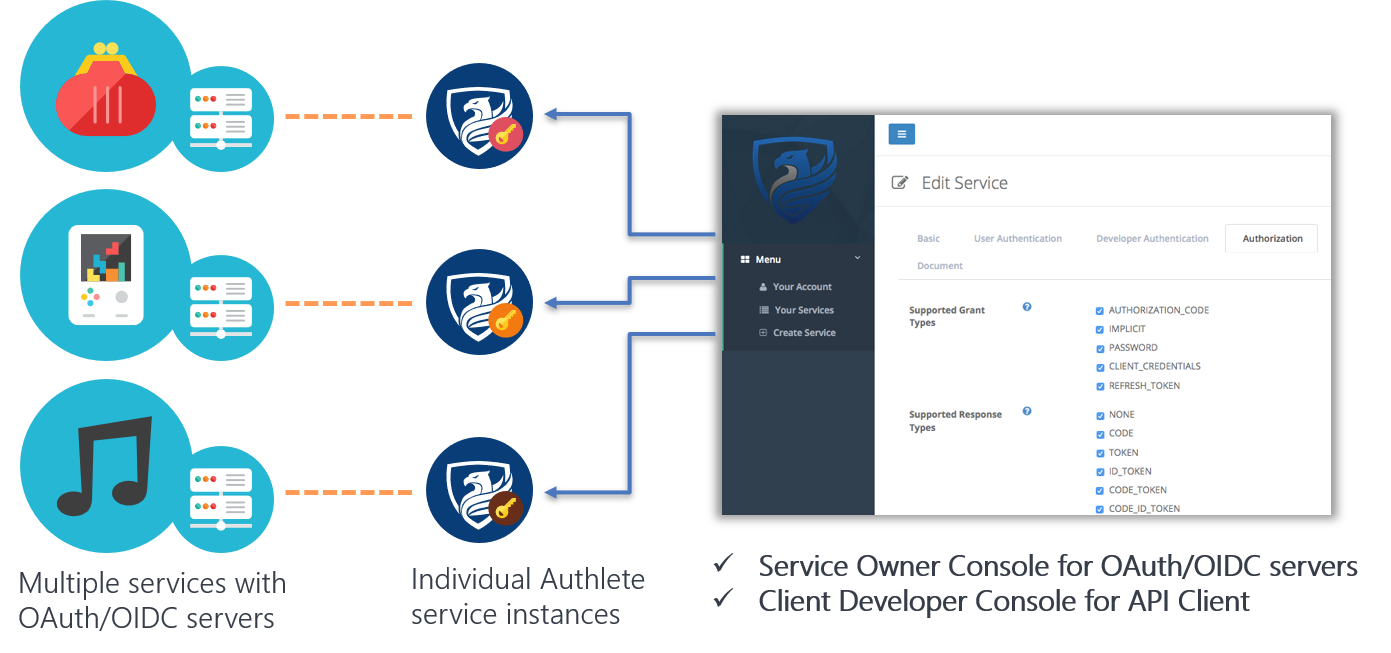
Authlete can run and manage multiple instances of OAuth 2.0 & OpenID Connect servers simultaneously, which can be managed by consoles.
It is easy to set up new instances: an architect therefore can place multiple authorization servers in a system wherever appropriate without a huge development cost. For example, an architect may have a separate authorization servers for smartphone applications from internal services.
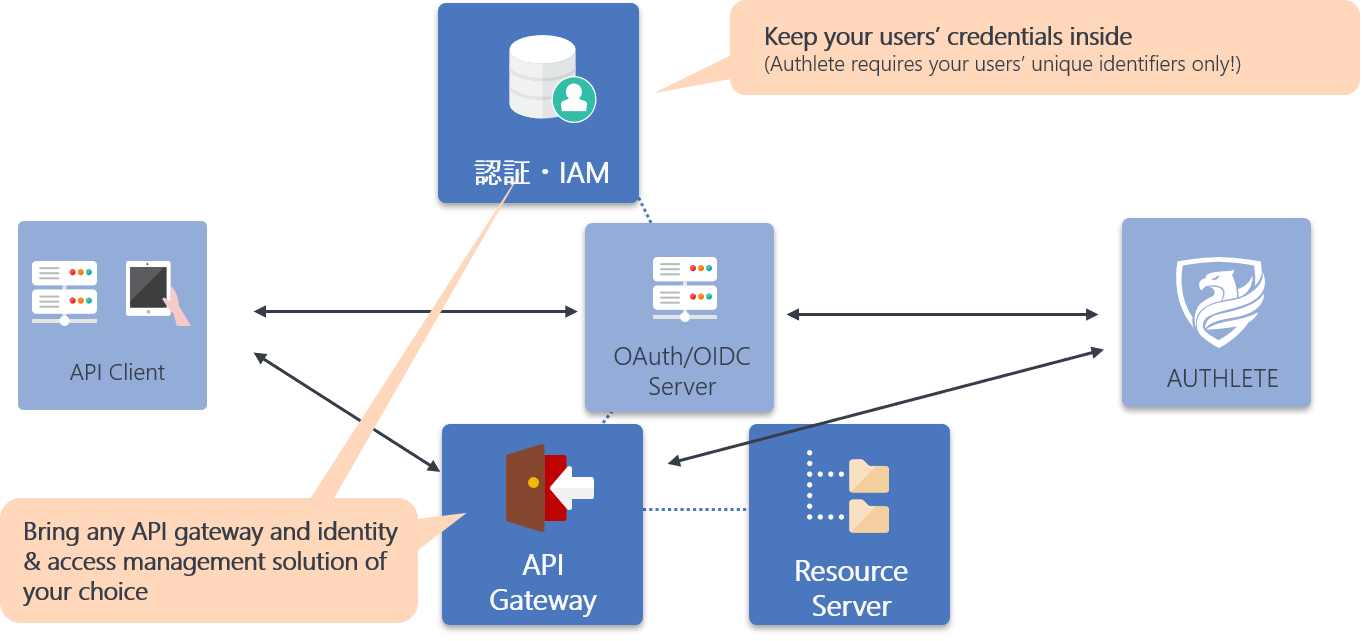
You can integrate Authlete with any IAM solution, authentication solution or API gateway solution of your choice because Authlete focuses on authorization function only. For example, if you have a authentication and IAM systems for your existing service, you can minimize the cost of introducing OAuth and OpenID Connect by integrating Authlete into those systems.
Authlete receives subjects of end-users from your system and associates the subjects with access tokens and other data. Therefore, you don't have to share your end-users credentials with us, which is quite unique compared with other API authorization solutions.
Authlete supports many specifications. Here is the list of the specifications (some specs are only available for ENTERPRISE plan).
Commercially Available
Available Soon
Authlete offers useful functionalities to deploy, implement and maintain systems that support OAuth and OpenID Connect protocols.
Open all tabs | Close all tabs
Responses from Authlete APIs contain a result code and result message.
An example is "[A011308] The host of the redirect URI must be 'localhost' when the client's application type is 'native' and the scheme of the redirect URI is 'http'.", which will help developers solve issues and reduce time to implement OAuth & OpenID Connect using Authlete.
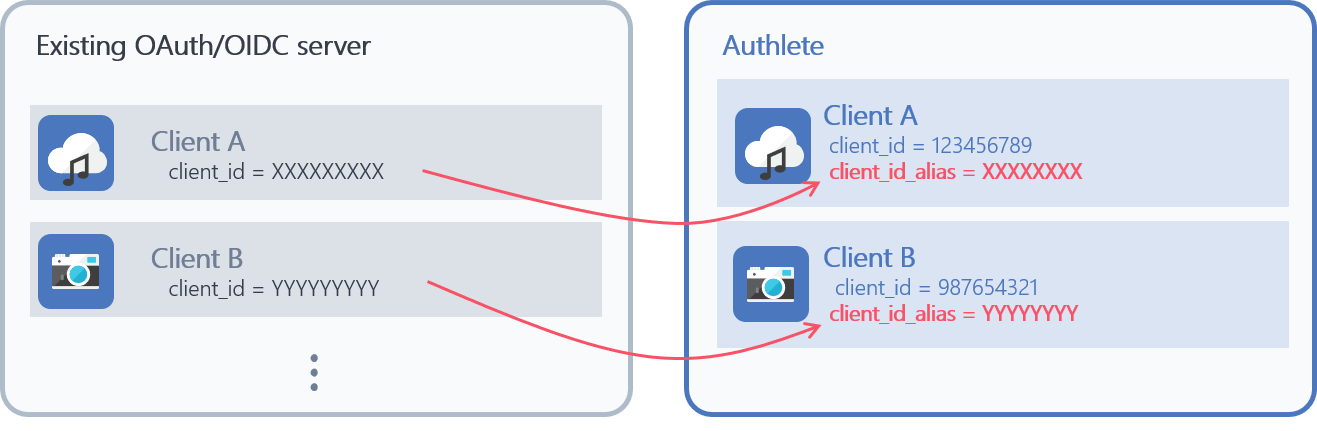
Authlete allows each client to have a client ID alias in addition to the client ID.
This function would be useful when you migrate from the existing authorization server to Authlete and keep using the existing client IDs in the new Authlete system.
Please refer to this document for more details.
Authlete provides a feature that enables an authorization server to associate arbitrary properties with either an access token or authorization code. The authorization server can easily share the properties with resource servers so that they can consume such information for its authorization enforcement as well as making a response.
For example, you would like to develop a money transfer API that can process specific transaction like "send $50 to ABC shop." You could implement such function by creating a "send-50dollar-to-abcshop" scope, but it hardly works as you would have to prepare a lot of scopes that are multiplied with recipients and amounts.
With the properties feature of Authlete, The authorization server can associate the money transfer information (or its handle, if database manages the actual information) with an access token to be issued to a client. The resource server, which hosts the money transfer API, receives an API request with the access token from the client, asks Authlete's introspection API to provide the properties along with details of the token, and then determines if the money transfer request is allowed to proceed.
Please refer to this document for more details.
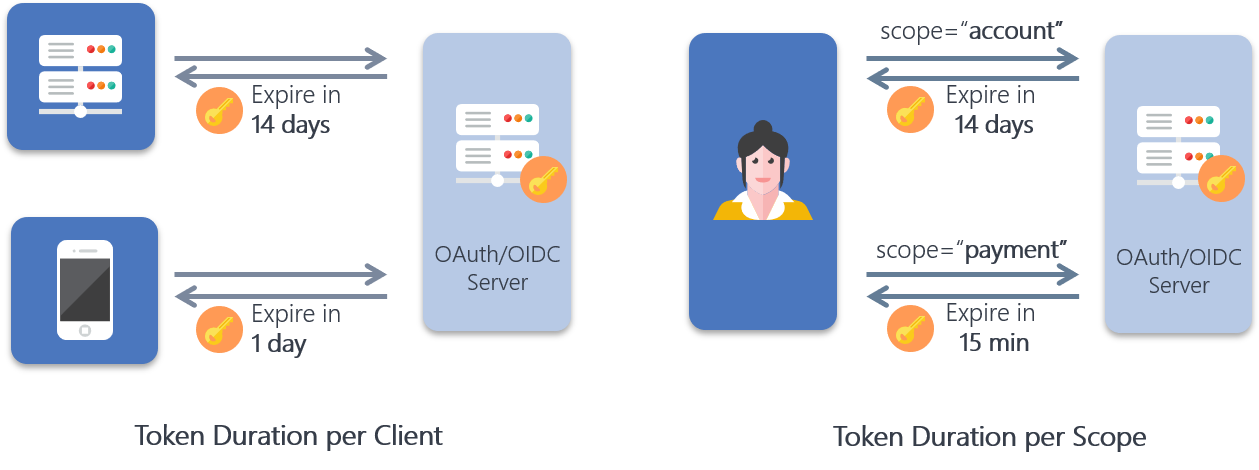
You can shorten the access token and refresh token duration per scope using the scope attribute functionality.
To activate this feature, set up a scope that has a scope attribute with its key of access_token.duration or refresh_token.duration and value of a “shorter” token duration in second. The duration of the tokens with the scope will be the duration set in the scope attribute. Please refer to this document for more details.
Also, you can shorten the access token and refresh token duration per client by configuring from the client developer console.
Authlete offers an option to choose whether to keep or reissue refresh tokens when refreshing access tokens.
With this option, Authlete only accepts a request with code_challenge_method = S256 when using PKCE protocol.
You can configure this setting from the “Authorization” tab in the service owner console.
Authlete revokes issued tokens and issues a new access token every time the same user grants an authorization request from a client.
Authlete enables customers to get a list of (or remove) scopes that are granted end-users.
This function is only available for Enterprise Plan users.
Authlete can verify PKI chains based on pre-registered trusted root certificates when authenticating clients with tls_client_auth method.
The allowable clock skew between the server and clients is configurable in seconds.
Authlete can reject requests without binding_message request parameter in FAPI-CIBA protocols.
Authlete conforms several OpenID Provider (OP) Profiles of the OpenID Connect protocol. So far, Authlete has received the following certifications.
| OpenID Certification | Version | Categories |
|---|---|---|
| OpenID Provider | 1.1 ~ |
|
| 2.1 ~ |
|
|
| FAPI OpenID Provider | 2.1 ~ |
|
| 2.2 ~ |
|
|
| FAPI-CIBA Profile OpenID Provider | 2.1 ~ |
|
* : Authlete is the only certified implementation in the world as of Feb 3rd, 2020.
You can support OAuth 2.0 and OpenID Connect in your Web service if you use Authlete. Sign up and start with Getting Started document.