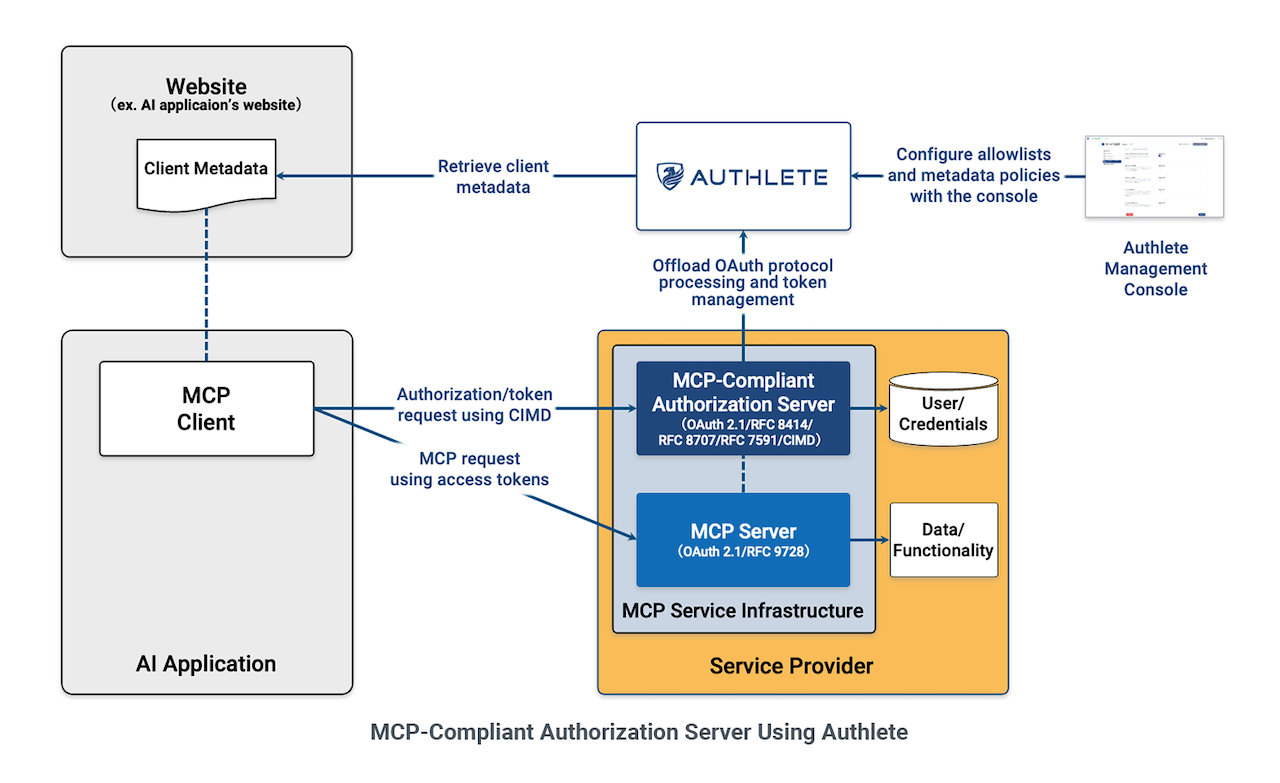

We’re pleased to announce that Authlete 3.0 has introduced support for OAuth Client ID Metadata Documents (CIMD) and a set of security- and developer-friendly features for building authorization servers compliant with the latest Model Context Protocol (MCP).
With Authlete, public institutions and service providers that offer data or functionality to AI agents via MCP—such as SaaS vendors, businesses leveraging data in healthcare, finance, and legal sectors, and retail/e-commerce operators—can securely and efficiently implement an OAuth-compliant authorization server in their MCP service infrastructure.
MCP is an open-source standard for connecting AI applications to external systems. Since its introduction by Anthropic in 2024, MCP has been adopted by companies such as Amazon Web Services, Cloudflare, Google, Microsoft, and OpenAI, and the latest version was released in November 2025.
Organizations that expose MCP servers on the internet must build OAuth-compliant authorization servers to securely grant access to MCP clients used by customers and partners.
In addition to CIMD, Authlete supports all OAuth specifications adopted by the latest MCP, including OAuth 2.1 (IETF Draft), Authorization Server Metadata (RFC 8414), Dynamic Client Registration Protocol (RFC 7591), and Resource Indicators for OAuth 2.0 (RFC 8707).
CIMD enables an authorization server to retrieve client metadata from the URL a client presents during the OAuth authorization flow, eliminating the need for traditional client pre-registration. This approach is particularly useful for MCP environments, which are designed for dynamic federation between clients and authorization servers.
Implementing CIMD for authorization servers requires not only enabling “dynamic client registration,” but also mechanisms to prevent unintended client registrations and appropriately process retrieved client metadata. Therefore, in addition to CIMD-compliant APIs, Authlete provides the following proprietary features:
Authlete provides the following configurations to streamline the development of authorization servers.
For details on these features, refer to the developer documentation.
Try Authlete for free to build an MCP-compliant authorization server: https://console.authlete.com/register.