
There are many CIAM solutions available today, such as IDaaS and IAM software packages. It may seem easy for service providers to find the optimal solution among these many choices.
However, it is worth noting that typical CIAM solutions take an all-in-one approach, integrating all functions. It’s necessary to cover all the components that make up CIAM, from user authentication to consent management to access control, in order to take full advantage of implementing such a solution.
This may not matter if you can build CIAM from scratch or easily migrate from an existing CIAM. On the other hand, if you’ve already built and run some of the CIAM functionality, or if you don’t want to expose authentication information represented by passwords to third-party providers such as IDaaS, you may not be able to take full advantage of the rich functionality offered by the CIAM solution. In other words, you may not get the return on your investment.
Furthermore, even if you need to enhance your CIAM infrastructure in response to business growth, it would be difficult to go beyond the solution’s specifications. A typical example is extending OAuth/OIDC. Extended specifications such as FAPI, mTLS, DPoP, PAR, RAR, and practices such as OAuth 2.0 Security Best Current Practice are still being actively developed in this area. However, not many CIAM solutions are able to keep up with these changes.
Most importantly, delegating everything to a CIAM solution means that the first important interaction with users - “user authentication and consent” - is out of the company’s control. For continuous improvement and enhancement of the user experience, this is not a good approach. It is critical to control the CIAM infrastructure within the organization and understand the customer touchpoints, to evolve CIAM in response to changing business needs and improve customer satisfaction.
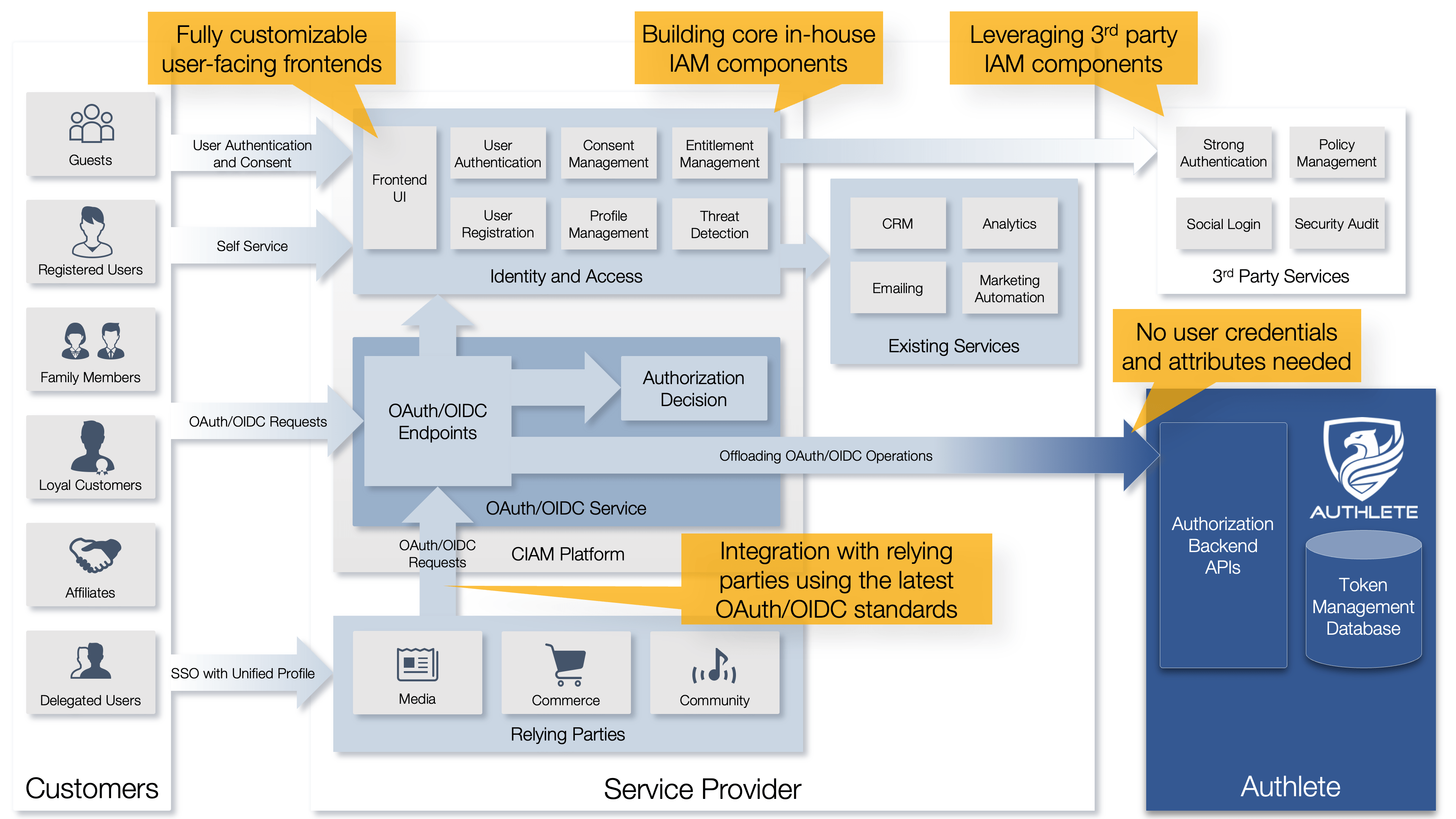
Service providers can rely on Authlete to eliminate the challenges of “OAuth/OIDC protocol processing” and “token lifecycle management” that are difficult to solve when developing and operating CIAM in-house. Since Authlete is designed to operate entirely as a backend service, service providers are free to build user-facing frontends, such as login screens and profile management, using Authlete’s API.
In addition, Authlete does not interact with or depend on other CIAM functions such as user authentication, consent management, and access control. This allows service providers to choose whether to in-house or outsource CIAM on a function-by-function basis, rather than as an entire infrastructure.
Authlete keeps up with the latest OAuth/OIDC specifications, allowing service providers to build a CIAM infrastructure that complies with industry-standard specifications without having to implement and operate it themselves.
As Authlete operates entirely in the backend, service providers can maintain full control over UI/UX aspects such as user authentication and consent.
The Authlete API is environment agnostic, allowing service providers to implement a CIAM infrastructure using their preferred language and framework.
Authlete offers three types of service systems: shared cloud, dedicated cloud and on-premises packages, allowing you to choose the form of deployment according to the scale and features of CIAM.